
Prepared for Prof. Javed I. Khan
Department of Computer Science, Kent State University
Date: June 2006
Abstract: With advent of Business-to-Business (B2B) and
Business-to-Consumer (B2C) interaction, it is has become a necessity
that information must be exchanged in a secure and accurate way. Most
of the web application contains security vulnerabilities which enables
attacker to exploit them and launch attack. As a result of attack
confidentiality, integrity and availability of information are lost.
This attacks which are at application level, cannot be prevented using
packet inspection firewall which analyses individual IP packets for
signature or allow specific ports. What is needed is mechanism which
analyses whole message stream
. In addition to that specific application level attack requires
specific mechanism. Attacks like content spoofing cannot be stopped
unless user is made aware.
In this survey, I would be discussing the different types of attack in
web applications at application level and ways to prevent them.
Other
Survey's on Internetwork-based Applications
Back to Javed I. Khan's Home
Page
Table of Contents:
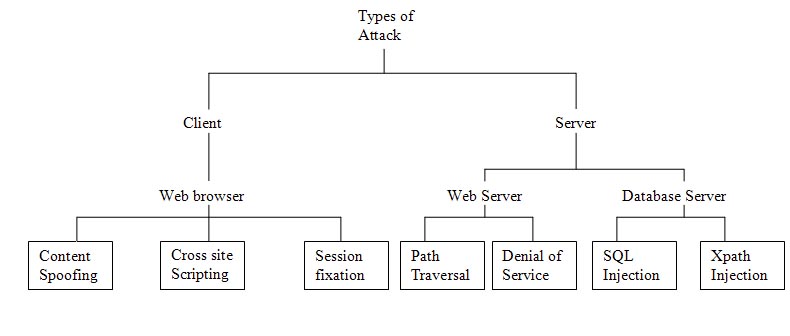
Fig.1 Types of attack
Rapid growth of internet has created many services, which have become integral part of our day to today life. Web applications are used for making reservations, paying bills, and shopping on-line. However wide spread usage of this applications came with increase in number and type of attacks affecting confidentiality, integrity and availability of information. Almost everyday a new security vulnerabilities are discovered which are exploited by hackers in accessing confidential information.
Need for securing web applications
Web application Architecture and attacks targeting different components
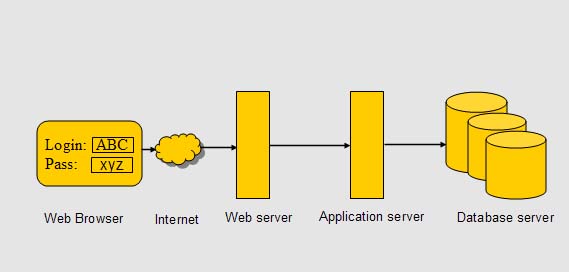
Fig. 2 Typical web application architecture
Web system consists of web browser at user end. User is connected to web application through internet. A firewall protects web system from intrusion and allows traffic at port 80 only. Web server receives request from browser, processes them and passes dynamic part to application server, which processes server side code, like JSP. All requests for database access are passed to database server. The results are shipped back to web browser
Web based system like this are subjected various attacks, targeting web server, database server and web browser. Users at client side using web browser to access web sites are targeted by hackers through content spoofing, cross site scripting and session fixation attack. Server side systems consisting of web server and database server are subjected different kinds of attack. Web server is targeted to path traversal attack which is used to read contents of restricted files and directories, other form of attack like denial of service attack prevents legitimate user from accessing service. Attacks at database server like SQL injection and Xpath injection aims to obtain unauthorized information.
Attacks at application level differ from network layer attack. Application level attack exploit vulnerabilities present in web application code and limitations of protocol like HTTP. Attacks at application level cannot be stopped by most network firewalls. They normally leave port 80 open for web server. It is through this port that web application communicates to the user. If the attacker is able to access application he may launch attack which cannot be prevented by firewall. For example, consider a user who has legitimate account at banking system. He connects to his account by authenticating and establishing a valid session. If the user is injecting code to access unauthorized information of other users, than network firewall will not be able to stop him. Preventing them requires fixing vulnerabilities in application code, like validating user input at server side rather than client side. Specific application level attack at application layer requires specific mechanism
Client side attacks are used for variety of purposes like stealing username and password, stealing cookies, which are used for session management, and accessing other sensitive information. To achieve all these tasks, attackers would sometimes create fake website with look similar to original website, and than they would send link of that fake website to victims email address asking him to open it and verify account information. In other form of client attack, attacker would submit malicious code in forums, message boards. When these are read by other users, the malicious code would execute in user's browser to access sensitive information like cookies which are than sent to attacker's machine.
In this type of attack malicious hackers would create fake website with look similar to original one to make user believe that the site is legitimate. They would create fake website for banks such as Citibank, online organization such as PayPal and eBay. Attacker would than send specially crafted links through email, instant messages to user. The messages may look quite authentic, having corporate logos and formats similar to the ones used by legitimate messages. Typically they would ask for verification of certain information such as account numbers and passwords. These links would make user believe that the content is coming from trusted website, but in fact they would be from external source. Sometimes also called phising, they are frequently used to get credit card or bank account information from user. Content spoofing tem is formally used in literature, phising term used more in media. The attack uses trust relationship between user and website. In most of the cases attacker would collect all information in two to three days and than would shut down his server to avoid being caught. Sometimes they are present in some other countries which makes it difficult to arrest them.
Example
Content spoofing can be done if web page is dynamically generated
using frames. Location of frame can be specified by URL parameter
value. Attacker can change this value to take user to different web
page. If the original URL is
http://abc.example/page?frame_src=http://abc.example/file.html
The attacker would replace frame_src parameter to take user to
different link.
http://abc.example/page?frame_src=http://attacker.example/foreign.html
The user would believe that content is coming from original domain, but in fact he is directed to attacker system.

Fig3. Content Spoofing
In this example, victim receives an email which asks him to click on "here" , which according to email would take user to banking site, so that user can verify his information. The attacker would create exact replica of citibank home page to fool user. After getting all information from user, he is directed to real site.
Dangers involved
What can be done
In cross-site scripting (XSS) malicious code is executed in user’s browsers which are usually written in VBScript, ActiveX, java etc. The code is echoed by web site to user’s browser. The code is placed in web site by attacker using message boards, bulletins etc. When these pages are viewed by user, the script present in messages is executed at user end. These scripts may read, modify or transmit data accessible by client’s browser.
Example
Consider a website which redirects user Alice after login to www.abc.com/default.asp?name=alice and a server-side script generates a welcome page that says "Welcome Back Alice!". The user information are stored in a database, and the Web site places a cookie on your computer containing a key to that database. The cookie is retrieved anytime the site is visited. An attack can be launched as follows:
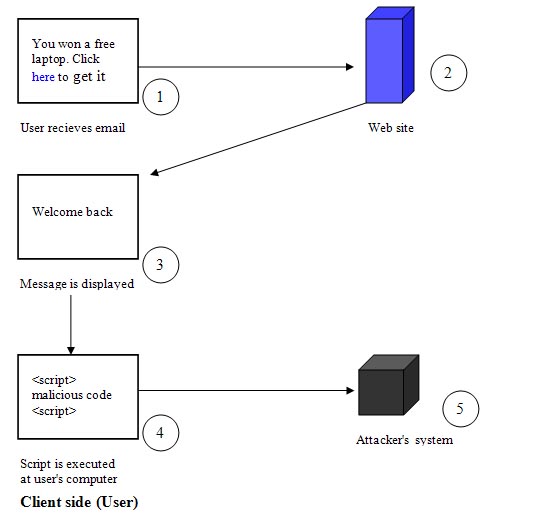
Fig. 4 Cross site scripting
Dangers involved
What can be done
HTTP was designed purely for document exchange. It is incapable of session management. It does not provide any way for web server to maintain states for user's subsequent requests. To perform session management web server generates session identifier which is sent to user's browser. In each subsequent request web browser sends this session identifier (sessionid) back to web server. Session ID thus can be used to identify users.
In session fixation attack, attacker fixes the Session ID of victim. Since the session ID, which is used by the victim, is fixed by attacker, attacker is able to access account of the victim by using same session ID to connect to his account without any authentication. Session fixation allows attacker to get access to the application with same privileges of the user whose session he steals.
The session fixation attack is normally a three step process :
1) Session set-up
The attacker connects to website to obtain session ID, which would be
introduced in user's browser.
2) Session fixation
The attacker introduces the session value obtained in last step into
the users browser by making him click on a URL containing session ID
which is obtained in last step (The URL link can be sent by attacker to
victim). When the user clicks on URL sent by attacker, his session ID
is fixed to the session ID value contained in URL.
3) Session entrance
The attacker waits until the user logs into the target web site. When
the user does so, the attacker also logs in same account using same
session ID. The attacker is able to do that since he knows the session
ID being used by victim.
The details of this attack be understood by an example which is given with a diagram showing all steps of attack.
Example
Consider web server online.worldbank.dom which hosts a web banking application. Session IDs are transported from browser to server within a URL argument session id. The attacker – who in this case is also a legitimate user of the system – logs in to the server

Fig. 5 Session fixation
Dangers involved
What can be done
Server side attack target web server for downloading or viewing files like scripts, configuration files without proper authorization. They use path traversal attack to achieve this file disclosure.
Other form of web server attack like denial of service attack prevents legitimate user from using service by flooding web server with messages. Due to heavy traffic and limited capacity the web server's resource are exhausted and is unable to process request of legitimate user.
Server side attack like SQL injection and Xpath injection target database server to retrieve information without proper authentication and authorization. Both these attack are possible when application uses user input to dynamically generate query without sanitizing them
Web servers generally allow access to a specific portion of the Web server's file system called the "Web document root" directory. In path traversal attack, attacker accesses files and directories that are outside web document directory. They do this by using special character sequences in URL input parameter like ../ which allows to access parent folder of a subfolder.
Example
Simple path traversal attack uses ". . /" character sequence in URL
move one directory above current directory, but recent web server
prevent this technique, so attacker using Unicode-encoding ". .%255c"
for backslash characters to escape filtering.
E.g., Attack against web server
http://webp/ . .%255c/script/
In some cases web application loads text from static file to render
web page. Like URL below uses home variable to load index page.
http://webpage/update.cgi?home=index.htm
The attacker can change URL parameter to replace index.htm with
update.cgi to get source code of script update.cgi.
http://webpage/update.cgi?home=update.cgi
Dangers involved
What can be done
Denial of service attack aims to prevent legitimate users from using a service. This is usually done by consuming all of a resource used to provide the service like CPU, operating system memory etc. Attacker may launch attack by bombarding website with numerous messages. If the attack is carried out by thousands of machines, than it is called distributed denial of service attack. DDoS is more complex and harder to solve. High volume of packet traffic makes it difficult to inspect legitimate from attack packet.
This how denial of service attack take place
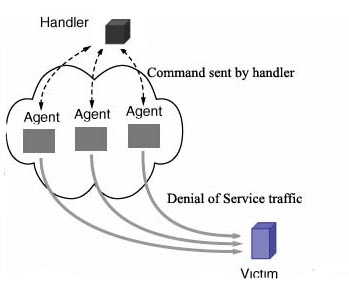
Fig.6 Denial of Service attack mechanism
Attacker builds a handler/agent network, where the attacker controls the network by issuing commands to the handler, which in turn relays commands (sometimes using a different command set) to the agents.
Example
A web server takes a certain amount of time to serve web page requests, which limits the maximum number of requests which can be handled by web server in a finite amount of time. If it is assumed that a web server can process 1000 requests per second to retrieve file and serve home page, than at most 1000 customer's request can be processed concurrently. Normally the web server receives 50-70 requests per second, which is less than 10 percent of its capacity. If attacker controls 10,000 machines and makes them send request every 10 second, than web server will receive 1000 request per second which when combined with normal traffic makes total request 1050-1070 request which exceeds the maximum capacity that web server can handle. The web server is not able to handle legitimate requests because of saturation .
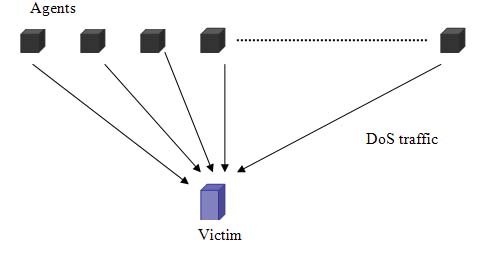
Fig. 7 Example of denial of service attack
Dangers involved
What can be done
In this kind of attack, attacker manipulates input parameters to inject malicious code which executes at server side to perform operations violating security of data.SQL injection and Xpath injection are two different kinds of attack under this category targeting database. Xpath injection is more severe, since the attacker is able access to all information, unlike SQL injection where the administrator can restrict user from accessing all information. Xpath as same syntax , unlike SQL where, different vendors have different syntaxes.
They are most prevelant form of attack since most of the website use database to store and retrieve data. In SQL injection attacker provides user input which becomes part of SQL query. Dynamically generated query when executed on database server without proper check could let attacker retrieve aunthorized information without proper authentication and authorization.
Example:
Consider a website which requires user to provide login name and
Password to access account information. The user name and password is
used by middle tier (ASP, servlets etc) to generate SQL statement.
Therefore, if a user submits login and password as “abc” and “xyz,” the
servlet dynamically builds the query: SELECT info FROM users WHERE
login=’abc’ AND pass=’xyz’
If attacker enters “’ OR 1=1 --” and “”, instead of “abc” and “xyz”,
the resulting query is:
SELECT info FROM users WHERE login=’’ OR 1=1 --’ AND pass=’’
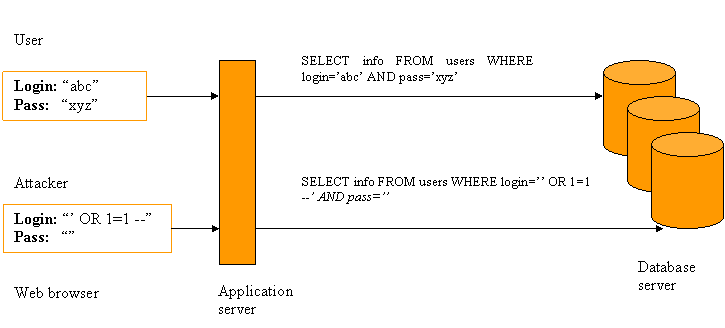
Fig.8 SQL Injection
Dangers involved
What can be done
XPath is used to query XML database. XML database is represented using an XML document and XPath query is similar to an SQL query. XPath queries are used for search requests, for login processing, for data retrieval, and other lightweight database tasks. XPath injection takes place in web site, which constructs XPath from User input.
Example:
Consider a XML document with three elements: User name, password and checking account number. The XPath expression to retrieve account number requires user to give user name and password :If the attacker enters following string in username field: ' or 1=1
or ' '=' , the Xpath expression would be:
string(//user[name/text()='' or 1=1 or ' '=' ' and
password/text()='xyz']/account/text())
Since 1=1 is a tautology, the attacker can login as first user listed in XML document.
Dangers involved
Dangers involved in Xpath injection is even more severe than SQL injection.
What can be done
Defending against XPath Injection is essentially similar to defending against SQL injection
| Attacks | Target | Effects | Severity | Prevention |
| Content Spoofing | Client | Loss of confidential information like username and password | moderate | Educating user |
| Cross site Scripting | Client | Unauthorized access to client's private information like cookies | moderate | Disabling scripts at client's browser |
|
Session fixation |
Client | Unauthorized access to user account information | moderate |
Issuing session id after authentication |
| Path traversal | Server | Unauthorized access to files and directories stored on server. | moderate | checking "../" and its variants. |
| Denial of Service | Server | Web application unavailable for normal users | moderate | Fixing bugs, reverse turing test, resource replication |
|
SQL injection |
Server |
Unauthorized operations and access to database. |
Severe |
checking user input, giving minimum privileges |
| Xpath injection | Server | Unauthorized access to all data entities. | Severe | checking user input |
We surveyed some of the application level attacks in web based systems which are present due to vulnerabilities present in configuration, and protocols standards.
Vulnerabilities present due to web server configuration leads to path traversal attack. In case of database server it leads to code injection attack. Improperly written server side code which fails to sanitize user input is another reason for these attacks. The fact that the applications are written by people who are different from people who manage security leaves vulnerabilities in codes. Operating systems and web browsers are getting more complex with each release. The sheer size of code makes it difficult to find all bugs and fix them on time.
Limitations of existing protocols are another reason for attacks.For example, HTTP not provide any way for web server to maintain states for user's subsequent requests. Existing methods for providing sessions have limitations which allows attacker to launch session based attacks.
There are different mechanism for preventing each type of application level attacks. Despite all efforts attacker would come up with new pattern and web applications would be continued to attack.